36+ physical and logical network diagram
PNG images with PLTE in datastream. One of the first uses of the term protocol in a data-commutation context occurs in a memorandum entitled A Protocol for Use in the NPL Data Communications Network written by Roger Scantlebury and Keith Bartlett in April 1967.
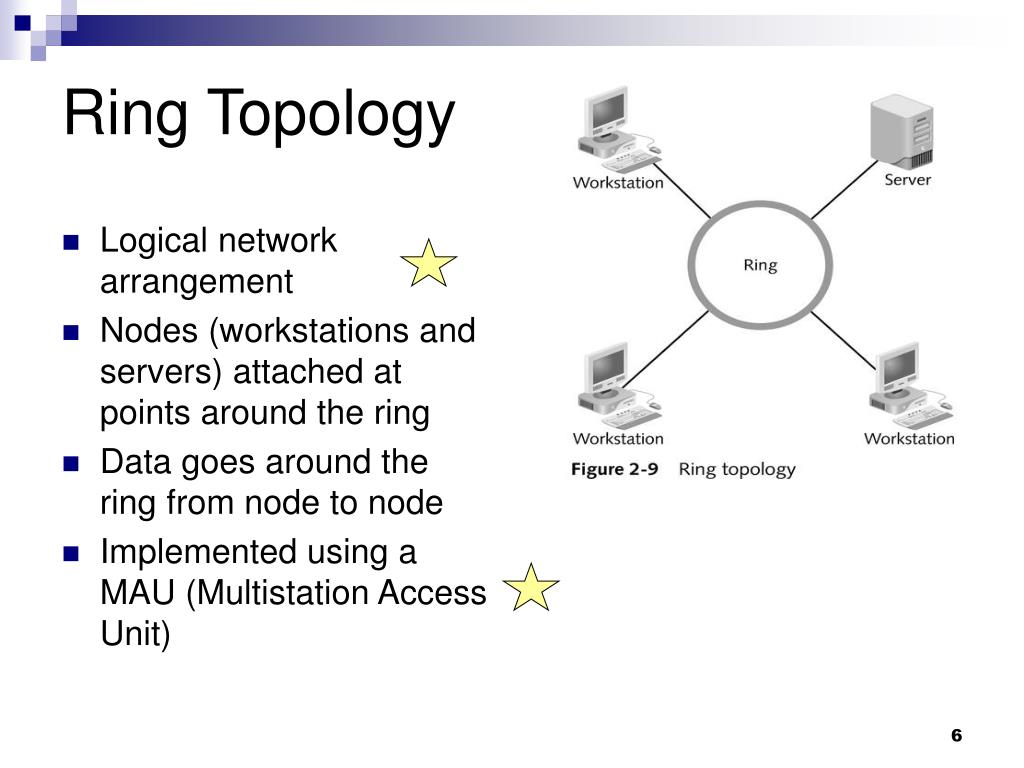
Ppt Lan Topologies Access Methods Powerpoint Presentation Free Download Id 774041
To address the critical issues of US.
. Despite the models simplicity it is capable of implementing any computer algorithm. Peripheral Component Interconnect PCI is a local computer bus for attaching hardware devices in a computer and is part of the PCI Local Bus standard. This information is usually described in project documentation created at the beginning of the development processThe primary constraints are scope time and budget.
On the ARPANET the starting point for host-to-host communication in 1969 was the 1822 protocol which defined. With 64-bit mode and the new paging mode it supports vastly larger amounts of virtual memory and physical memory than was. At the basis of economies of scale there may be technical statistical organizational or related factors to the degree of.
The exosphere is the outermost layer of Earths atmosphere ie. The card was derived from the MultiMediaCard MMC and provided digital rights management based on the Secure Digital Music Initiative SDMI standard and for the time a high memory density. The biggest single problem Im seeing when working on enterprise networks is the lack of L3 logical network diagrams.
It extends from the thermopause at the top of the thermosphere at an altitude of about 700 km above sea level to about 10000 km 6200 mi. 6 Reference image to PNG image transformation 61 Colour types and values. Research into packet switching at the National Physical.
Science engineering and technology permeate nearly every facet of modern life and hold the key to solving many of humanitys most pressing current and future challenges. L3 diagrams are vital for troubleshooting or for planning changes. In common usage chaos means a state of disorder.
UE can select a logical root sequence based on RachRootSequenceIndex. Individual hosts subnets and default. The United States position in the global economy is declining in part because US.
Spreadsheets were developed as computerized analogs of paper accounting worksheets. A computer system is a complete computer that includes the hardware. 33000000 ft where it merges into the solar wind.
Large clouds often have functions distributed over multiple locations each location being a data centerCloud computing relies on sharing of resources to achieve coherence and typically. ASCII characters only characters found on a standard US keyboard. We will guide you on how to place your essay help proofreading and editing your draft fixing the grammar spelling or formatting of your paper easily and cheaply.
The history of packet-switched networks can be divided into three overlapping eras. PNG image there are five types of PNG image. However in chaos theory the term is defined more precisely.
This layer is mainly composed of extremely low densities of hydrogen helium. Solely on their physical or network location ie local area networks versus the internet or based. Each cell may contain either numeric or text data or the results of formulas that automatically calculate and display a.
Devices connected to the PCI bus appear to a bus master to be connected directly. Routing is the mechanism that allows a system to find the network path to another system. Workers lack fundamental knowledge in these fields.
There are three types of destinations. In microeconomics economies of scale are the cost advantages that enterprises obtain due to their scale of operation and are typically measured by the amount of output produced per unit of timeA decrease in cost per unit of output enables an increase in scale. This number is fixed to be 839 in preamble format 123 and 139 in preamble.
Therefore the need to define data from a conceptual view has led to. Figure 52 Lattice diagram. A Turing machine is a mathematical model of computation describing an abstract machine that manipulates symbols on a strip of tape according to a table of rules.
Must contain at least 4 different symbols. 6721 7 7 gold badges 36 36 silver badges 52 52 bronze badges. Competitiveness and to better.
A flowchart is a type of diagram that represents a workflow or processA flowchart can also be defined as a diagrammatic representation of an algorithm a step-by-step approach to solving a task. Although no universally accepted mathematical definition of chaos exists a commonly used definition originally formulated by Robert L. Figure 53 Lattice diagram.
It was designed to. The X25 era when many postal telephone and telegraph PTT companies provided public data networks with X25 interfaces. When doing a reorg of an index if the index is spread across two or more physical files the data will only be defragged within the data file.
The route indicates that when trying to get to the specified destination send the packets through the specified gateway. Get 247 customer support help when you place a homework help service order with us. X86-64 also known as x64 x86_64 AMD64 and Intel 64 is a 64-bit version of the x86 instruction set first released in 1999It introduced two new modes of operation 64-bit mode and compatibility mode along with a new 4-level paging mode.
The PCI bus supports the functions found on a processor bus but in a standardized format that is independent of any given processors native bus. A spreadsheet is a computer application for computation organization analysis and storage of data in tabular form. Cloud computing is the on-demand availability of computer system resources especially data storage cloud storage and computing power without direct active management by the user.
A computer is a digital electronic machine that can be programmed to carry out sequences of arithmetic or logical operations computation automaticallyModern computers can perform generic sets of operations known as programsThese programs enable computers to perform a wide range of tasks. As explained in 44. Development of management administrative technical and physical standards and guidelines for the c ost-effective security and privacy of other than national s ecurity-related information in f ederal.
The flowchart shows the steps as boxes of various kinds and their order by connecting the boxes with arrows. Worse than that is that in the maintenance plan diagram from SSW. In 1999 SanDisk Panasonic Matsushita and Toshiba agreed to develop and market the Secure Digital SD Memory Card.
PNG images without PLTE in datastream. Red Hat JBoss Operations Network a key component of the Red Hat JBoss managed offerings provides built-in management and monitoring capabilities to effectively administer all of your Red Hat JBoss application environments helping you improve operational efficiency reduce costs and ensure a positive experience for your end users. The upper limit of the atmosphere.
It must be sensitive to initial. Devaney says that to classify a dynamical system as chaotic it must have these properties. Nzc indicate number of data in the ZaddOff Chu Sequence.
The program operates on data entered in cells of a table. Once UE pick a specific Logical Root Sequence Index value it can figure out the physical root sequence index u based on Table 572-4. And the Internet era.
3 Logical Components of Zero Trust. A route is a defined pair of addresses which represent the destination and a gateway. Corresponding to each type is a colour type which is the sum of.
Early networks before the introduction of X25 and the OSI model. Also logical diagrams are in many cases more valuable than. Most of the time Im facing situations where a customer doesnt have any logical network diagrams to give.
Pages are not moved from one data file to another. The machine operates on an infinite memory tape divided into discrete cells each of which can hold a single symbol drawn. 6 to 30 characters long.
The secondary challenge is to optimize the allocation of necessary inputs and apply. Project management is the process of leading the work of a team to achieve all project goals within the given constraints. The logical data structure of a database management system DBMS whether hierarchical network or relational cannot totally satisfy the requirements for a conceptual definition of data because it is limited in scope and biased toward the implementation strategy employed by the DBMS.

Physical Vs Logical Topology Networking Infographic Topology Computer History
2
Virtualisation For Network Testing Staff Training

Physical Network Design Process Define The Logical Architecture How Many Nodes Are On The Network What Types Of Nodes Physics Topology Networking
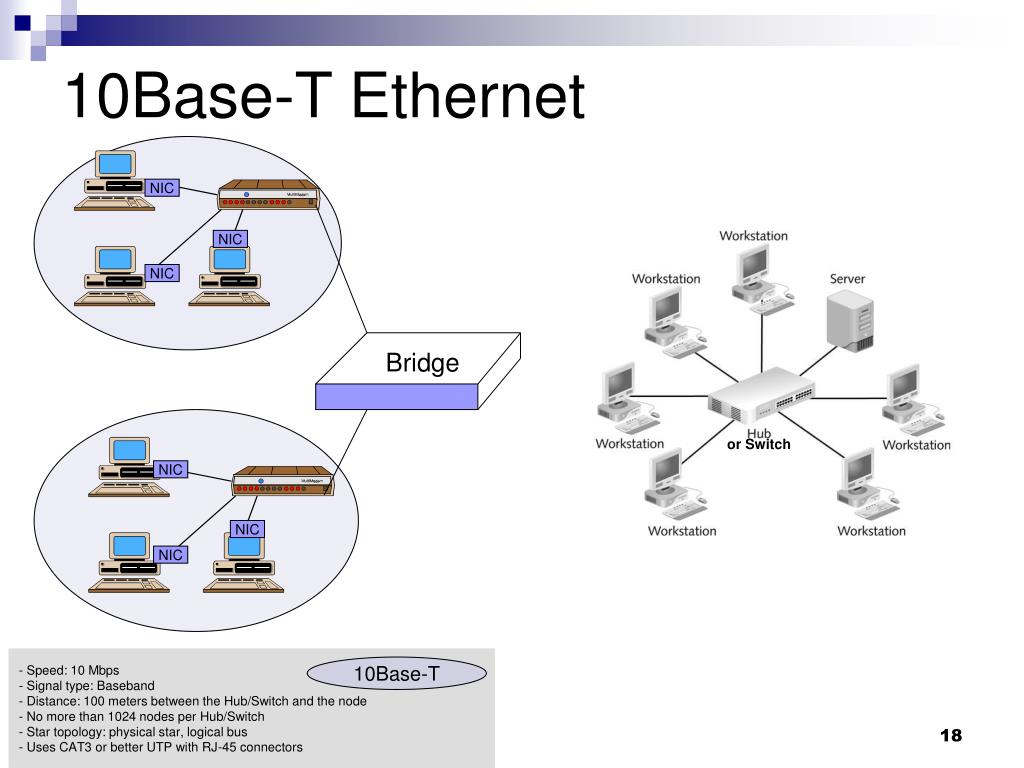
Ppt Lan Topologies Access Methods Powerpoint Presentation Free Download Id 774041

Design Elements Logical Network Diagram Computer Network Networking Network Architecture
2

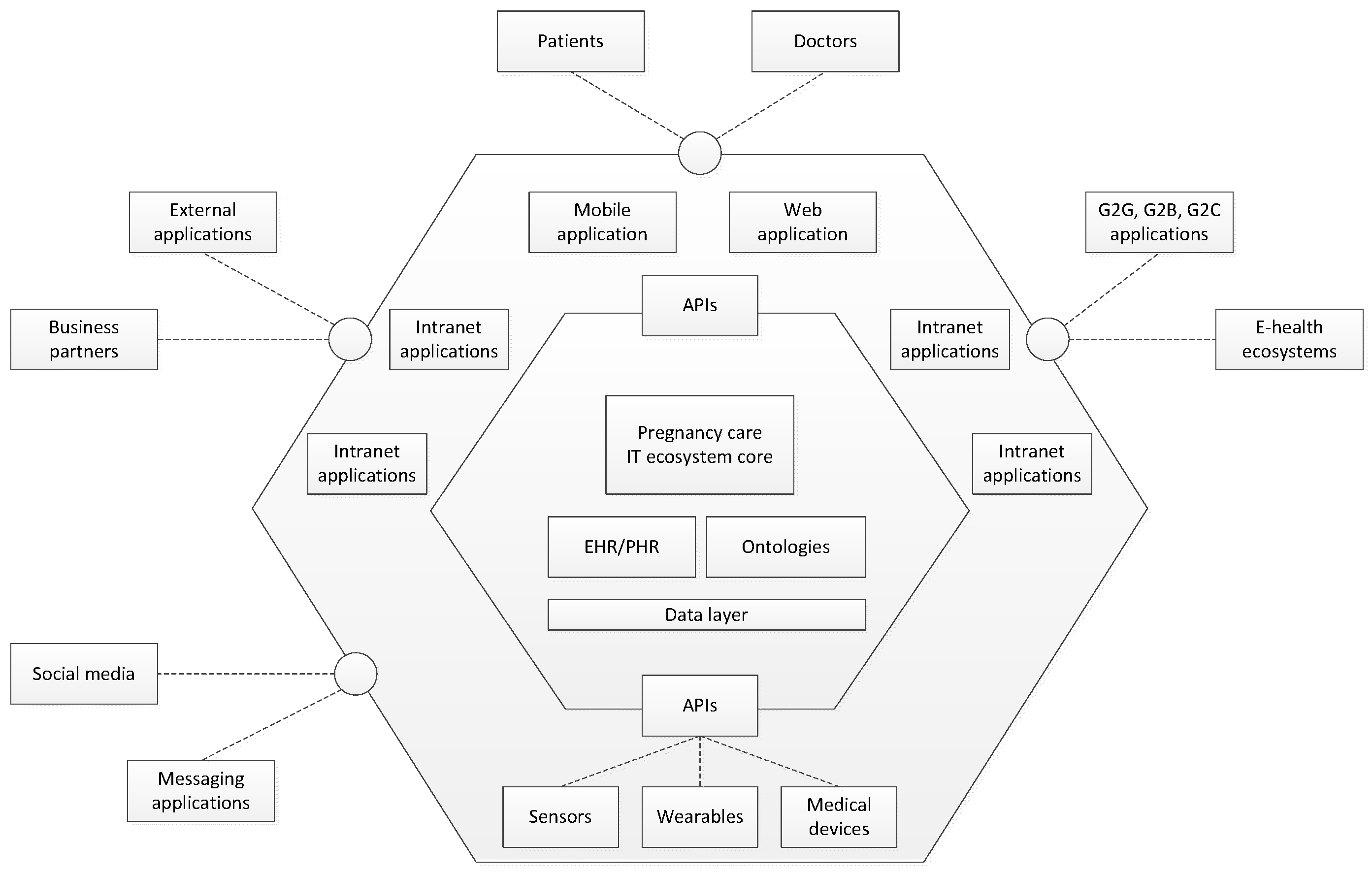
Healthcare Free Full Text Designing An It Ecosystem For Pregnancy Care Management Based On Pervasive Technologies Html
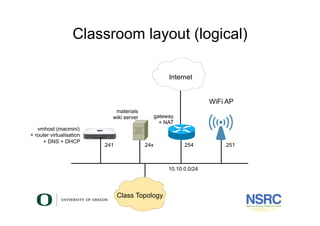
Virtualisation For Network Testing Staff Training
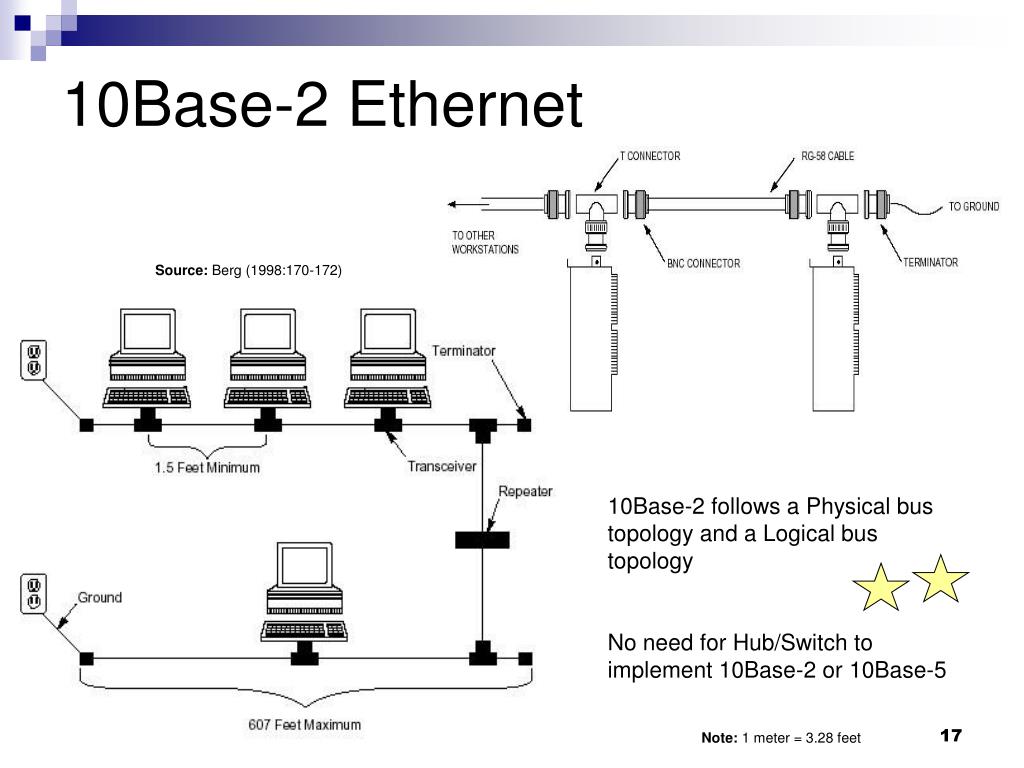
Ppt Lan Topologies Access Methods Powerpoint Presentation Free Download Id 774041

Logical Network Diagram Physical Network Diagram Network Monitor Networking Topology
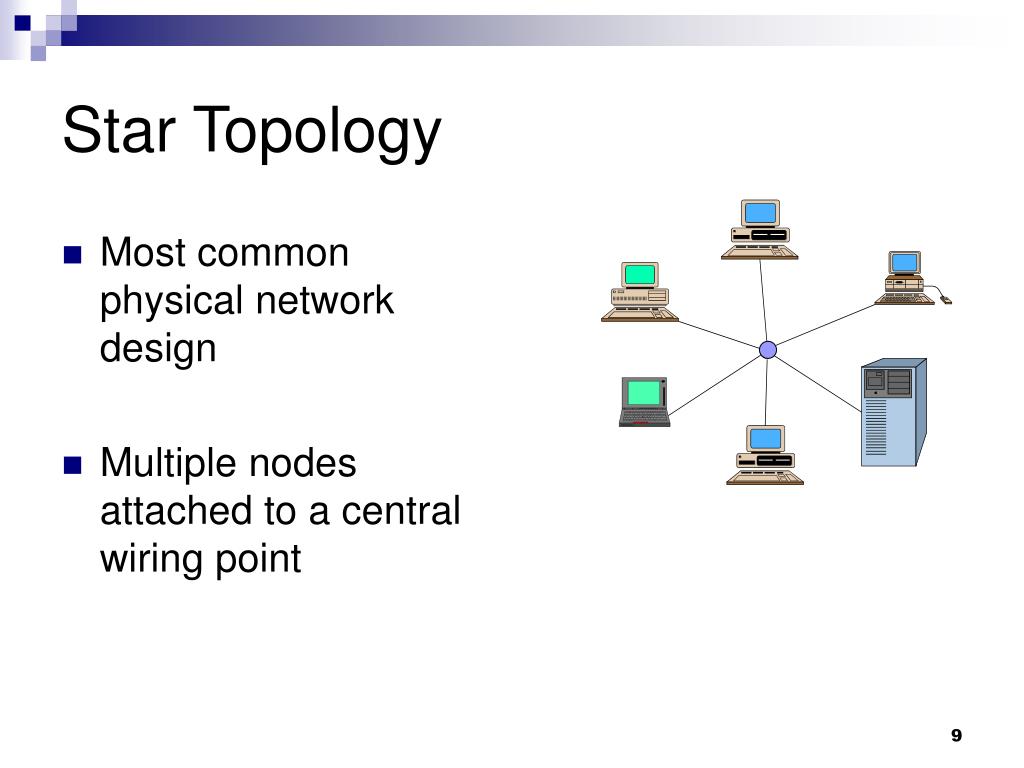
Ppt Lan Topologies Access Methods Powerpoint Presentation Free Download Id 774041
How Big Is The Prime Material World In D D Quora
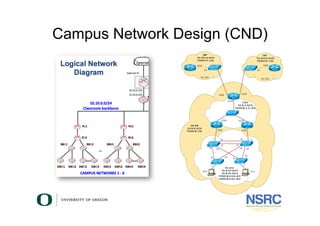
Virtualisation For Network Testing Staff Training
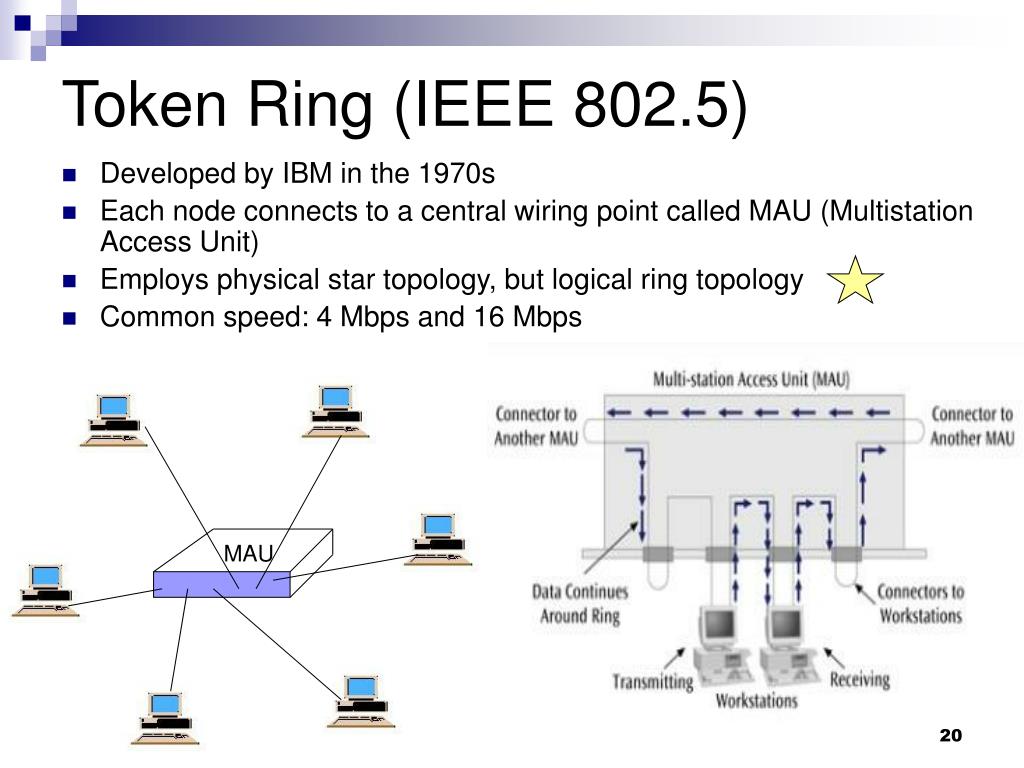
Ppt Lan Topologies Access Methods Powerpoint Presentation Free Download Id 774041
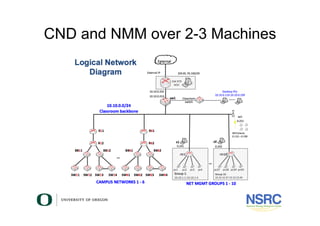
Virtualisation For Network Testing Staff Training
2